Hackers Wanted: $1M Bounties Entice White Hats to Hunt for DeFi Bugs
Should I just steal the money? There’s a vulnerability in the code… Of a DeFi protocol with $3B in TVL. I was just looking at the open-source code for fun. But now, it’s serious. There’s a bug bounty, a reward that pays out $10K to anyone who finds a major weakness. But exploiting this vulnerability…
By: Bailey Reutzel • Loading...
Hacks
Should I just steal the money?
There’s a vulnerability in the code… Of a DeFi protocol with $3B in TVL. I was just looking at the open-source code for fun. But now, it’s serious. There’s a bug bounty, a reward that pays out $10K to anyone who finds a major weakness. But exploiting this vulnerability would let me siphon off $2M in user funds. Seems pretty critical. $10K? Over $2M? It’s either rob or get robbed, right?
That’s the temptation hackers must wrestle with when they find vulnerabilities in crypto code. While there are bug bounty programs that recognize and compensate hackers who report bugs in project’s code, they typically don’t offer rewards that seem appropriate for the potential damage if the bugs were exploited. Plus, hackers, even white hats, can be treated like a nuisance or a threat, and some are outright dismissed.
Attractive Target
Immunefi is a nine-month old platform that’s jumped right into the middle of this dilemma. It connects crypto protocols with hackers and is aiming to professionalize a lawless badland in cybersecurity — DeFi. The reason is obvious: There’s a lot of money at risk right now. Sensational exploits like this week’s $600M hack of Poly Network — and the perpetrator’s decision to return much of the loot — are making headlines all the time.
“The DeFi space is literally the most attractive target to hackers there has ever been,” says Robert Forster, co-founder and CTO of Armor.Fi, a decentralized brokerage that provides protection coverage for DeFi assets. It posts $1M bounties on Immunefi.
That’s right, Armor is ready to pay $1M for finding a critical bug, and actually they already have, paying $1.5M to a hacker in February for a critical bug that put its reserves at risk.
“Our average payout is tens of thousands of dollars,” says Mitchell Amador, the co-founder and CEO of Immunefi. “It’s just orders of magnitude bigger than any other bug bounty platform.”
“The DeFi space is literally the most attractive target to hackers there has ever been.”
Robert Forster
Immunefi has raised the floor price for bug bounties throughout DeFi. Taking a look at the list of bounties available on Immunefi’s platform, we can see that xDai is offering rewards up to $2M (that’s with six zeros paid out for a single high quality bug report); Cream Finance is offering rewards up to $1.5M; SushiSwap has a bounty listed rewarding hackers up to $1.25M; and PancakeSwap and Sovryn join Armor in posting bounties on Immunefi for $1M.
These payouts are basically unheard of in the bug bounty world. Until now.
The Clash Between Computer Coders
The clash between hackers and protocol developers has been on vivid display.
PeckShield, a blockchain security company, recently reported a potential vulnerability to a protocol only to receive this disregard in response: “We have been audited by Techrate, project is over 2 month[s] old. We are okay, look for work somewhere else ?”
During the recent Poly Network exploit, the hacker or hackers said they could have stolen far more than they did, and weren’t interested in the money as much as delivering a lesson. And the hacker who exploited Thorchain also sent a note to the protocol explaining that they could have taken more, but wanted to minimize damage. The key line: “10% VAR bounty would have prevented this.”
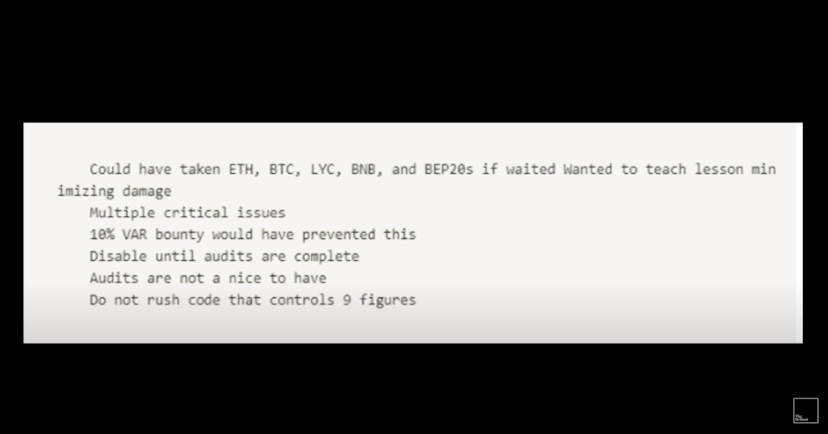
VAR stands for value at risk and is an estimate of the dollar value at risk of loss over a certain time period.
What’s particularly interesting about the hacker throwing out 10% is that it’s the amount Immunefi encourages its clients to offer to hackers who find critical bugs — 10% of the total value locked (TVL) in the protocol. Immunefi calls this a scaling bug bounty, and it’s what’s setting them apart in the bug bounty space.
If you’ve been paying attention to DeFi, you know 10% of TVL across many of these platforms is a huge chunk of money.
Only a couple days after the Thorchain attack, its second in a week, the protocol offered a $500,000 bug bounty on Immunefi. While this isn’t 10% — Thorchain has a little more than $100M TVL — more like 5%, it’s still a huge bounty.
No More Measly Money
Immunefi was set up in mid-December by three co-founders: Amador, Travin Keith and Duncan Townsend. Amador and Keith had met during their time working on NXT Foundation, which promotes and community manages NXT, a smart contract blockchain launched in 2013. Amador had already been working on DeFi security (or the lack thereof) with another man, who recommended Townsend as “the best security person.”
The team has raised money and bootstrapped the venture, but isn’t sharing more details about funding at the moment.

CEO Mitchell Amador is one of Immunefi’s three co-founders.
Checking one of Immunefi’s competitors and the most popular bug bounty platform in the software world, Hackerone, it appears Github used the platform to pay out $50,000 for a critical bug a few weeks ago. Otherwise, the bounties paid out and disclosed there are typically not even close to the $10K range.
But these small bounties just don’t cut it in crypto.
“It’s the combination of the amount of money in DeFi and the ease of cashing out that money and still being anonymous after and all the code is open source,” Armor’s Forster says. “It’s almost insane how perfect the industry is for hackers.”
Amador echoes that, saying, “The numbers are so gargantuan and the ability to get caught is so small, if you’re slightly less than extremely principled, there’s a huge temptation to walk.”
Black Hats Become White Hats
On top of the money, Immunefi streamlines the hacker/client engagement by handling all communication, coordination and negotiation, if necessary. They don’t require KYC, allowing hackers to remain anonymous if they choose, and if they’ve worn a black hat before, that might be attractive. Plus, Immunefi accepts payouts in crypto, adding flexibility for both clients and hackers.
“We act as a safe harbor for black hats to come to us and become white hats,” Keith of Immunefi told The Defiant.
What these big payouts have meant for Immunefi is huge growth. Since Immunefi launched with three clients, the company has onboarded 113 more.
Compare this to bug bounty platform, Yes We Hack, which launched a few years ago and has 100 clients. Immunefi has less clients than Hackerone, but definitely more in crypto.
“Immunefi is setting outstanding precedents,” says Kevin McSheehan, AKA pad, a black hat turned white hat hacker who’s familiar with Immunefi who has to yet participate in bounties on the platform. “They’re doling out unprecedented bounties and have [the crypto] niche covered. Gone are the days of sifting through Hackerone to find elusive blockchain programs.”
Your Code is Vulnerable
But it took some coaxing. Immunefi’s co-founders are crypto native, which helped. They did an enormous amount of outreach in the industry when the company first launched.
See, no developer wants to get a message saying, “Hey, your code is vulnerable.” Being the bearer of bad news, that hasn’t always gotten white hat hackers pats on the back and parades. And bug bounty programs are still so ad hoc that many protocols don’t assign anyone to specifically manage the reports. Those tasked with checking submissions have other jobs within the projects, and for sure, some of the submissions they go through are bullshit, which adds to the annoyance.
So Immunefi’s pitch was, “Hey, we know running bug bounty programs is hard, let us do it for you.” And it’s worked.
Even though hacks are rampant in DeFi, Immunefi has blocked a good amount. More than $3M in bounties have been paid out using the platform, averting more than $1B in damages, the company says. There’s currently $31M in bounties available on the platform. According to Amador, critical bugs are being found on about a quarter of Immunefi’s clients.
Full-Time Bounty Hunting
As an early mover in bounties tailored for crypto and DeFi, Immunefi wants to make bug hunting a viable career rather than just a hobby hackers pursue for fun in their spare time.
“The money is there for them to make this a full-time job,” Amador told The Defiant.
Sure enough, the hacker who received Armor’s $1.5M payout, Alexander Schlindwein said, “I hadn’t seen such high bounties for critical vulnerabilities before.” And these weren’t just the big, battle-tested protocols — these bounties were being offered by smaller players.
Schlindwein is the CTO of Ideamarket, so he’s got a full-time job, but surely making a million on a moonlight is pretty powerful.
“We act as a safe harbor for black hats to come to us and become white hats.”
Travin Keith, Immunefi
If big money entices more hackers into the bounty world full-time, that would strengthen protocol defenses, better protect clients’ assets, and address a critical weakness in the entire DeFi proposition.
“There’s such huge pressure to innovate and compete in DeFi that unfortunately, many protocols take on the risk of a vulnerability in the code than spend extra time testing and testing, making sure things are completely secure,” says Immunefi’s Keith.
Bug bounty programs like Immunefi’s offer a viable alternative to holding back a product launch. Boosting the payouts offers a fair value as an alternative to theft. In this way, bug bounties can act as a last line of defense in the smart contract security stack.
“I am certain that crypto/DeFi native bug bounty platforms like ImmuneFi play an integral role in improving the current situation of constant hacks and exploits,” Schlindwein said.
Advertisement
Get the best of The Defiant directly in your inbox 💌
Know what matters in Web3 with The Defiant Daily newsletter, every weekday
90k+ investors informed every day. Unsubscribe anytime.