Not Just a Bank Run: New Evidence Shows Iron Finance Crashed Due to Code Exploit
$2B of market value lost in even less time than what would be considered an “overnight disaster” will be recognized as one of DeFi’s darkest days. It would be pretty unbecoming if the people didn’t band together against centralized entities in Decentralized Finance which caused this debacle. But the people did, and with the official…
By: Herbert Eng • Loading...
Research & Opinion
$2B of market value lost in even less time than what would be considered an “overnight disaster” will be recognized as one of DeFi’s darkest days. It would be pretty unbecoming if the people didn’t band together against centralized entities in Decentralized Finance which caused this debacle.
But the people did, and with the official telegram group being constantly barraged by links to my little expose on Medium, Iron Finance was forced to respond two days ago with a compensation plan. Iron also stopped muting its telegram group, which it had repeatedly done in the past, even when its tokens were crashing. I dare say it was because they realized they couldn’t control what their stakeholders wanted to say in the unofficial group.
To recap the rise and fall of Iron Finance, Total Value Locked on the protocol peaked at over $3 billion on June 15, while TITAN, the protocol’s collateral token, rose over 100x since its launch to $6. Then on June 16, a few large sales kicked off a stampede for the exits, sending TITAN from $62 to nearly zero in just 16 hours as the IRON stablecoin lost its peg.
Now, the community is still looking for answers with some sleuthing about to identify any culprits. And some members are claiming they found a smoking gun.
Re-entrancy Vector
One of our hacktivists is a software engineer who performs technical audits on the security of blockchains. He has uncovered additional details into how the crash happened. He identified a “giant re-entrancy vector” in all three masterchef contracts. You can see the proof here if you search for “emergency” in the live source code:
0xa37dd1f62661eb18c338f18cf797cff8b5102d8e
0x65430393358e55a658bcde6ff69ab28cf1cbb77a
0xb444d596273c66ac269c33c30fbb245f4ba8a79d
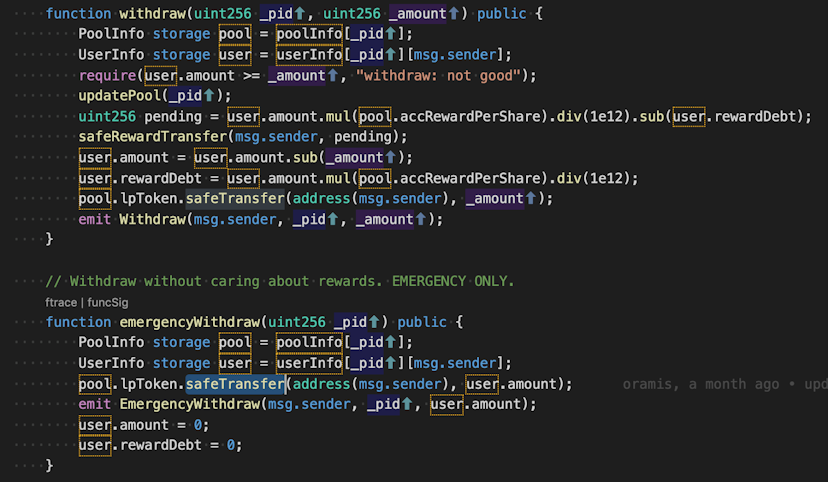
Smoke from the Masterchefs
The code structure is similar to that of cross-function reentrancy attacks, which have been a staple in DeFi exploits. By “similar” I mean only the names of the operants differ and the actual functionality is exactly the same.
This is a new revelation based on evidence that had not been uncovered by any audit effort, posthumous to the crash or otherwise. The facts show that the code was written in such a way to allow anyone to siphon off cash from the protocol.
Here is what our engineer says:
This can’t be an accident…
So to give a high level overview… the MasterChef contracts all have an emergencyWithdraw [function] that display the class re-entrancy attack… basically allowing unlimited funds to be siphoned.
The callers of this function have been tracked back in several cases to so-called “clearing house” addresses that basically do nothing but transfer their entire balances to other addresses. I think this is a smoking gun actually.
This is a transaction where an address successfully called the emergencyWithdraw function:
https://polygonscan.com/tx/0x05d5c121251cb7cea91a89aaa164451639acb328b4a0a8001470aea531d77a7a
Approximately $60,000 was sent out from this address.
This is only one example. There might be others who have abused reentrancy even earlier to have profited even more. What’s crucial here is anyone could have called emergencyWithdraw this way to withdraw funds from the pools — there is no ownership requirement to do this.
Still, and while this is highly speculative, it is very unlikely that the Iron developers did not know about this, especially since they made comments about it in the code.
Historically, DeFi has been plagued with three kinds of exploits. There is the migrator code, which requires masterchef ownership and is an internal call; the reentrancy function, which doesn’t require ownership and is an external call and hence free-for-all to abuse; and the third kind revolves around manipulations surrounding price oracles, which was detailed in my first article.
Iron’s fiasco already broached two of three exploit classes. Quite an “achievement” just like when they announced how their project became the world’s first bank run in the cryptographic universe.
Follow the Money, Round Two
The evidence detailed thus far provided enough justification to screen known dev addresses through multi-hop analysis.
This time, we looked at outbound transactions from the treasuryFund contract, which was where Iron’s developers received their allocated rewards in terms of $TITAN (30% of the supply of $TITAN was vested to the developers over a 36 month period).
We also noticed the contract still held approximately 454,474 TITAN (worth $0.00018), which might seem like a lot but is really chump change compared to the trillions of TITAN tokens on the open market.
We found one recipient who was selling all of his TITAN as he received it; his last trade netted a cool $220K. Funds from this wallet would then hop at least two more times. So we had to run the addresses of the recipients of funds from treasuryFund through multi-hop analysis to better visualize what was going on.
Unfortunately, only two wallets drew nonblank results (out of a total of 19 unique addresses) on the software we use (Bitquery does not yet support analysis within the Polygon network): Introducing 0x06cc87f6e3ef5578ab3e7c88bc43bae8f05ab55c (“55c”).
“55c” shares the same convoluted pattern of distribution I revealed in the previous article. You have a lot of interfacing with multiple intermediating wallets and multiple paths that end up in the same destination address, like a Binance account. Why would anyone take so much trouble to funnel funds in multiple directions towards the same account?
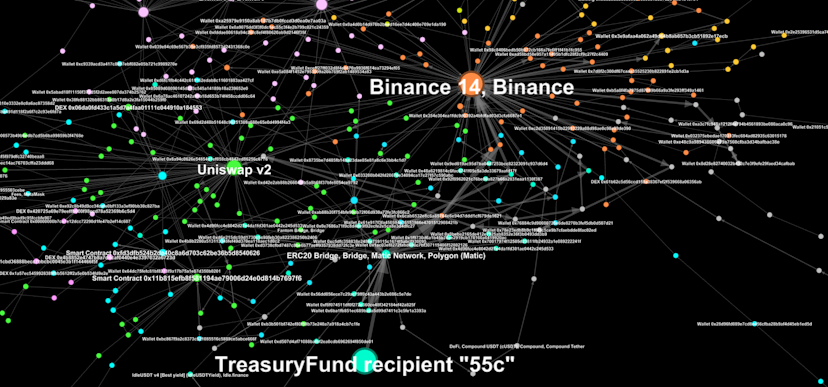
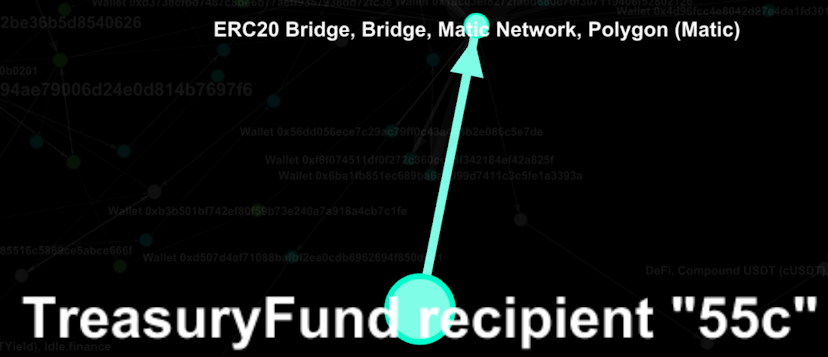
It begins with “55c” getting his funds off Polygon through the ERC20 bridge.
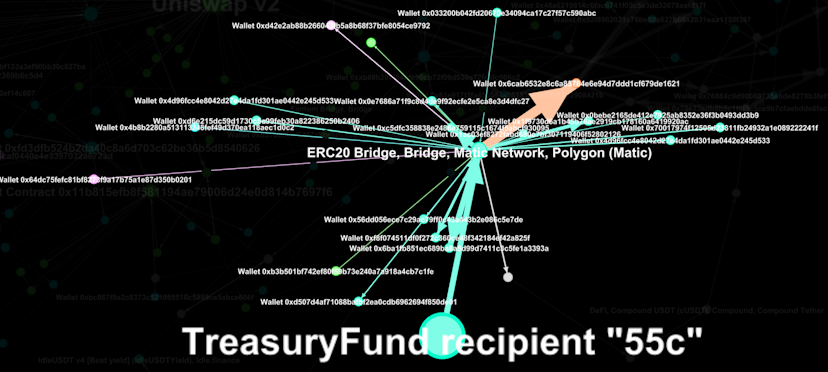
From there funds are sent to multiple wallets.
Running a bank is hard
What about the other wallet? 0xd1d075db389919a6985ddc9b32b5f3ad6f0869cd — “69cd”. Here’s what its polygonscan looks like:
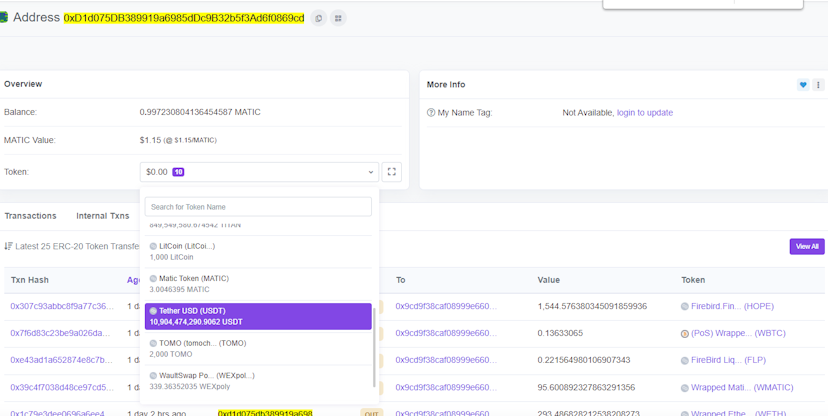
Nothing to see here, just 10.9 billion in Tether USD
Why does it hold ten billion in Tether USD? Investigator volunteers think this might actually be blockchain anonymizing service Tornado Cash. This signals Iron developers may be trying to conceal their funds.
Sure, you can’t conceal what is already not anonymous, but you can conceal funds that pass through Tornado Cash for projects in the future.
Norwegian Connection?
The community then took to the oldest doxing trick in the book — the WHOIS query. You can do this yourself, but all of the information is “redacted for privacy”.
Nothing a little cash cannot solve however. Paying for a historical “whois” search yielded actionable information (full credit to Michael Roterman). The full pastebin is provided here for everyone to peruse. Much of the more recent information had been redacted but you should scroll all the way down to line 1336 where you can find details of the first registered owner of the domain.
“registrantContact”: {
“name”: “Bjarn Zachrisson”,
“organization”: “Norsk Hedge Fond AS”,
“street”: “Setra Vei 18”,
“city”: “Oslo”,
“state”: “”,
“postalCode”: “0786”,
“country”: “NORWAY”,
“email”: “bjornzachrisson@gmail.com”,
“telephone”: “4546290000”,
“telephoneExt”: “”,
“fax”: “”,
“faxExt”: “”,
“rawText”: “Registrant Name: Bjarn Zachrisson\nRegistrant Organization: Norsk Hedge Fond AS\nRegistrant Street: Setra Vei 18\nRegistrant City: Oslo\nRegistrant Postal Code: 0786\nRegistrant Country: NO\nRegistrant Phone: +45.46290000\nRegistrant Email: bjornzachrisson@gmail.com”
},
Technically, the domain address Iron.Finance was registered under NORSK HEDGE-FOND AS, a limited liability company based in Oslo, Norway. Its reported profit before tax in the year 2019 stands at a measly $326.30, which is basically nothing.
As its name literally suggests, it is purportedly a hedge fund that deals in real estate. The associated contact person was one Bjørn Erik Zachrisson. At this point, there is nothing that indicatively connects Zachrisson to the Iron Finance we know; Zachrisson could know nothing and is simply the contact person for the domain address.
So we dug further using sources that cannot provide false information, such as patent offices and business entity regulatory bodies. More importantly, these can provide information about the present. Here is a patent filing by Zachrisson anyone can find from the Norwegian Industrial Property Office which reveals a second business entity Zachrisson is connected to, Harmonychain. Harmonychain is a publicly traded ($HMONY) nordic company based also in Oslo, Norway. It offers customers third party mining services that are environmentally-friendly. It also wants to build a mining supercomputer.
Community sleuths also found the cached website that Iron.finance was before it became the Iron.finance we lost money on.
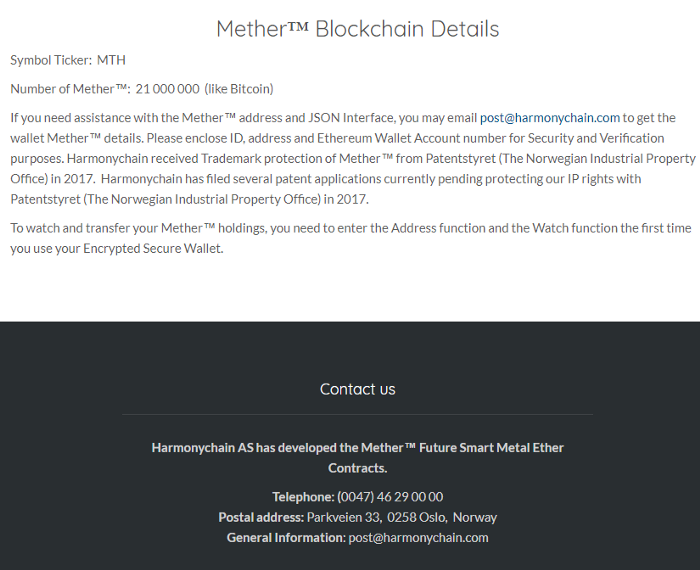
Introducing Mether, like Ether, but way more meth
It introduced “Mether”, presumably a crypto-synthetic asset that was backed by Iron as commodity futures. The site from this August 2018 snapshot is credited to a Harmonychain AS; coincidentally it has the same name as the one Zachrisson runs now in 2021.
Oslo-based news portal HegnarTV interviewed Zachrisson in 2017 too. For those who aren’t fluent in Norwegian, Zachrisson wanted to build crypto linked to 5% of the world’s commodities market and is interested in a strategy combining specifically iron and nickel.
Incidentally, the Harmony blockchain has also been audited by Peckshield, the same auditor that was tasked to audit Iron Finance on the 18th, two days after the fateful crash. Many in the community Telegram contacted Peckshield and Mr. Xuxian pretty much sends back the same answer to everyone who asked:
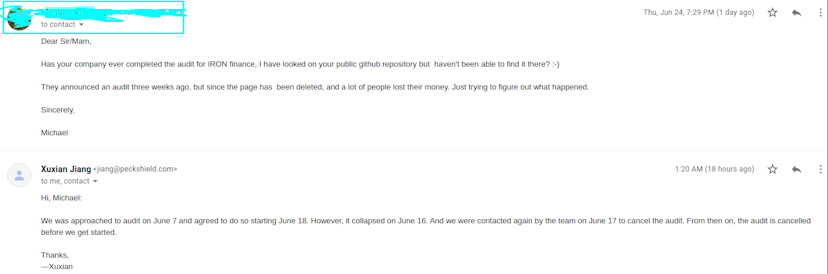
What we learned is that the Iron.Finance domain has changed hands from owner to owner, all of whompaid to have their WHOIS records redacted for privacy. Meanwhile its original registrant is now managing a company dedicated to crypto mining.
Mischievous members of the community started asking random questions on the official Telegram about Zachrisson, if he was a Star Wars fan and if his real identity is a pirate named Captain Barnacles. They got banned.
Another thing stood out from metadata on the public github repository Iron.finance is using.
Author: Oramis <76583172+oramis1008@users.noreply.github.com>
Date: Mon Jun 14 15:39:44 2021 +0700
commit 9ad46beeca5dd97a826e7728933d2328eedb978b
Author: h3xag0nx <jem.dyke12@gmail.com>
Date: Mon Jun 14 15:14:59 2021 +0700
Here is the list of countries at UTC +0700: Russia, Mongolia, Australia, Cambodia, Indonesia, Laos, Thailand, Vietnam. It sounds like Iron was using outsourced code houses from overseas. Certainly there is nothing wrong with that, but it is concerning if you had to wake up developers who are sleeping while the markets crash and $2B goes to zero.
Call to Action
There’s a lot more to uncover. For example, no one has accorded enough scrutiny to what happened to the valuation of Iron’s other cryptos, like $DND, its mutant derivatives and their associated pools. These also faced the same shorter-than-overnight value depreciation over the same time period on a different blockchain.
This story isn’t just about the historic mess that is Iron Finance, it is about how the future of finance matures with calibrated self-regulation, civic advocacy and media outreach that isn’t just empty sensationalism. You can start by contributing information on the community Telegram.
Because otherwise, we all go back to 0.5% APY.
Advertisement
Get the best of The Defiant directly in your inbox 💌
Know what matters in Web3 with The Defiant Daily newsletter, every weekday
90k+ investors informed every day. Unsubscribe anytime.